CS315 Assignment 1 Solution and Discussion
-
Assignment No. 01
Semester: Fall 2019
Network Security-CS315 Total Marks: 20Due Date: 15/11/2019
Instructions:
Please read the following instructions carefully before submitting assignment:
You need to use MS word document to prepare and submit the assignment on VU-LMS.
It should be clear that your assignment will not get any credit if: The assignment is submitted after due date.
The assignment is not in the required format (doc or docx)
The submitted assignment does not open or file is corrupt.
Assignment is copied (partial or full) from any source (websites, forums, students, etc)Objective:
To learn about Network Security Requirements and administrative tasks.
Assignment
Question 1: Marks 10
Consider the following scenarios and identify which Security Requirements could be applied to each of scenario.
1- A Dr finds that the patient history is wrong. Hospital information software DETECTS from its log that a nurse has altered that history of patient.
2- ATM service is down since morning.
3- Ali did not use his credit card on Sunday but still he received an email which tell him that his credit card has been used.
4- A student has got his university card, but with a picture of some other student on it.
5- The personal information provided by the customer on web page do not match with his actual NIC that he is carrying.
Question # 2 on next page.Question 2: Marks 10
Keeping in mind the different administrative approaches for information security and expected attack for information retrieval, you are required to select the correct option in column B for each case of column A. Write your option in column C.
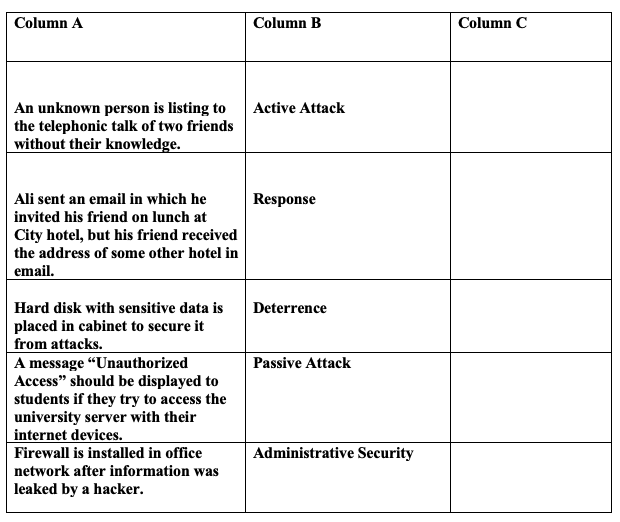
Best of Luck!
-
Assignment No. 01
Semester: Fall 2019
Network Security-CS315 Total Marks: 20Due Date: 15/11/2019
Instructions:
Please read the following instructions carefully before submitting assignment:
You need to use MS word document to prepare and submit the assignment on VU-LMS.
It should be clear that your assignment will not get any credit if: The assignment is submitted after due date.
The assignment is not in the required format (doc or docx)
The submitted assignment does not open or file is corrupt.
Assignment is copied (partial or full) from any source (websites, forums, students, etc)Objective:
To learn about Network Security Requirements and administrative tasks.
Assignment
Question 1: Marks 10
Consider the following scenarios and identify which Security Requirements could be applied to each of scenario.
1- A Dr finds that the patient history is wrong. Hospital information software DETECTS from its log that a nurse has altered that history of patient.
2- ATM service is down since morning.
3- Ali did not use his credit card on Sunday but still he received an email which tell him that his credit card has been used.
4- A student has got his university card, but with a picture of some other student on it.
5- The personal information provided by the customer on web page do not match with his actual NIC that he is carrying.
Question # 2 on next page.Question 2: Marks 10
Keeping in mind the different administrative approaches for information security and expected attack for information retrieval, you are required to select the correct option in column B for each case of column A. Write your option in column C.

Best of Luck!
Q.1
Consider the following scenarios and identify which Security Requirements could be applied to each of scenario.Q.1 Solution:
1- A Dr finds that the patient history is wrong. Hospital information software DETECTS from its log that a nurse has altered that history of patient.- Accountability
2- ATM service is down since morning.
- Availability
3- Ali did not use his credit card on Sunday but still he received an email which tell him that his credit card has been used.
- Confidentiality
4- A student has got his university card, but with a picture of some other student on it.
- Integrity
5- The personal information provided by the customer on web page do not match with his actual NIC that he is carrying.
- Authenticity
Q.2
Keeping in mind the different administrative approaches for information security and expected attack for information retrieval, you are required to match the case of column A to the column B.
Q.2 Solution:
-
Assignment No. 01
Semester: Fall 2019
Network Security-CS315 Total Marks: 20Due Date: 15/11/2019
Instructions:
Please read the following instructions carefully before submitting assignment:
You need to use MS word document to prepare and submit the assignment on VU-LMS.
It should be clear that your assignment will not get any credit if: The assignment is submitted after due date.
The assignment is not in the required format (doc or docx)
The submitted assignment does not open or file is corrupt.
Assignment is copied (partial or full) from any source (websites, forums, students, etc)Objective:
To learn about Network Security Requirements and administrative tasks.
Assignment
Question 1: Marks 10
Consider the following scenarios and identify which Security Requirements could be applied to each of scenario.
1- A Dr finds that the patient history is wrong. Hospital information software DETECTS from its log that a nurse has altered that history of patient.
2- ATM service is down since morning.
3- Ali did not use his credit card on Sunday but still he received an email which tell him that his credit card has been used.
4- A student has got his university card, but with a picture of some other student on it.
5- The personal information provided by the customer on web page do not match with his actual NIC that he is carrying.
Question # 2 on next page.Question 2: Marks 10
Keeping in mind the different administrative approaches for information security and expected attack for information retrieval, you are required to select the correct option in column B for each case of column A. Write your option in column C.

Best of Luck!
@zareen said in CS315 Assignment 1 Solution and Discussion:
1- A Dr finds that the patient history is wrong. Hospital information software DETECTS from its log that a nurse has altered that history of patient.
With the advent of audit trail programs, organizations can precisely monitor who has had access to patient information.
Administrators can even detail what reports were printed, the number of screen shots taken, or the exact location and computer used to submit a request. Alerts are often set to flag suspicious or unusual activity, such as reviewing information on a patient one is not treating or attempting to access information one is not authorized to view, and administrators have the ability to pull reports on specific users or user groups to review and chronicle their activity. Software companies are developing programs that automate this process. -
Assignment No. 01
Semester: Fall 2019
Network Security-CS315 Total Marks: 20Due Date: 15/11/2019
Instructions:
Please read the following instructions carefully before submitting assignment:
You need to use MS word document to prepare and submit the assignment on VU-LMS.
It should be clear that your assignment will not get any credit if: The assignment is submitted after due date.
The assignment is not in the required format (doc or docx)
The submitted assignment does not open or file is corrupt.
Assignment is copied (partial or full) from any source (websites, forums, students, etc)Objective:
To learn about Network Security Requirements and administrative tasks.
Assignment
Question 1: Marks 10
Consider the following scenarios and identify which Security Requirements could be applied to each of scenario.
1- A Dr finds that the patient history is wrong. Hospital information software DETECTS from its log that a nurse has altered that history of patient.
2- ATM service is down since morning.
3- Ali did not use his credit card on Sunday but still he received an email which tell him that his credit card has been used.
4- A student has got his university card, but with a picture of some other student on it.
5- The personal information provided by the customer on web page do not match with his actual NIC that he is carrying.
Question # 2 on next page.Question 2: Marks 10
Keeping in mind the different administrative approaches for information security and expected attack for information retrieval, you are required to select the correct option in column B for each case of column A. Write your option in column C.

Best of Luck!
@zareen said in CS315 Assignment 1 Solution and Discussion:
Assignment No. 01
Semester: Fall 2019
Network Security-CS315 Total Marks: 20Due Date: 15/11/2019
Instructions:
Please read the following instructions carefully before submitting assignment:
You need to use MS word document to prepare and submit the assignment on VU-LMS.
It should be clear that your assignment will not get any credit if: The assignment is submitted after due date.
The assignment is not in the required format (doc or docx)
The submitted assignment does not open or file is corrupt.
Assignment is copied (partial or full) from any source (websites, forums, students, etc)Objective:
To learn about Network Security Requirements and administrative tasks.
Assignment
Question 1: Marks 10
Consider the following scenarios and identify which Security Requirements could be applied to each of scenario.
1- A Dr finds that the patient history is wrong. Hospital information software DETECTS from its log that a nurse has altered that history of patient.
2- ATM service is down since morning.
3- Ali did not use his credit card on Sunday but still he received an email which tell him that his credit card has been used.
4- A student has got his university card, but with a picture of some other student on it.
5- The personal information provided by the customer on web page do not match with his actual NIC that he is carrying.
Question # 2 on next page.Question 2: Marks 10
Keeping in mind the different administrative approaches for information security and expected attack for information retrieval, you are required to select the correct option in column B for each case of column A. Write your option in column C.

Best of Luck!
In the networking system information communicates in communicational lines .Normalinformation transmission will communicate in the traditional type of however confidentialinformation might transmit within the kind of encrypted form o that no-one will hack the directionfrom communicational lines. The banking sector is one in all the vital sector wherever all sort ofmonetary data send through the communicational lines and it desires the high security ofknowledge. Varied encryption algorithms are a unit want to defend the info among a networkfor electronic communication. Automated teller machines is additionally associate degree examplewherever we’d like high security of knowledge in terms of knowledge communication fromAutomated teller machines to bank Server and contrariwise
-
Assignment No. 01
Semester: Fall 2019
Network Security-CS315 Total Marks: 20Due Date: 15/11/2019
Instructions:
Please read the following instructions carefully before submitting assignment:
You need to use MS word document to prepare and submit the assignment on VU-LMS.
It should be clear that your assignment will not get any credit if: The assignment is submitted after due date.
The assignment is not in the required format (doc or docx)
The submitted assignment does not open or file is corrupt.
Assignment is copied (partial or full) from any source (websites, forums, students, etc)Objective:
To learn about Network Security Requirements and administrative tasks.
Assignment
Question 1: Marks 10
Consider the following scenarios and identify which Security Requirements could be applied to each of scenario.
1- A Dr finds that the patient history is wrong. Hospital information software DETECTS from its log that a nurse has altered that history of patient.
2- ATM service is down since morning.
3- Ali did not use his credit card on Sunday but still he received an email which tell him that his credit card has been used.
4- A student has got his university card, but with a picture of some other student on it.
5- The personal information provided by the customer on web page do not match with his actual NIC that he is carrying.
Question # 2 on next page.Question 2: Marks 10
Keeping in mind the different administrative approaches for information security and expected attack for information retrieval, you are required to select the correct option in column B for each case of column A. Write your option in column C.

Best of Luck!
@zareen said in CS315 Assignment 1 Solution and Discussion:
Ali did not use his credit card on Sunday but still he received an email which tell him that his credit card has been used.
The credit card company can decide you owe the disputed amount when there’s a disagreement between you and a merchant over a charge you agreed to. But in a case where you didn’t authorize the charge, there is more protection available for you. If your credit card was stolen and then used to make purchases, the company can’t make you pay more than 50 of the unauthorized amount, as the Federal Trade Commission explains. And if only the card number was stolen, so that you are still holding on to the physical card, you’re not obligated to pay any unauthorized charges.
-
Assignment No. 01
Semester: Fall 2019
Network Security-CS315 Total Marks: 20Due Date: 15/11/2019
Instructions:
Please read the following instructions carefully before submitting assignment:
You need to use MS word document to prepare and submit the assignment on VU-LMS.
It should be clear that your assignment will not get any credit if: The assignment is submitted after due date.
The assignment is not in the required format (doc or docx)
The submitted assignment does not open or file is corrupt.
Assignment is copied (partial or full) from any source (websites, forums, students, etc)Objective:
To learn about Network Security Requirements and administrative tasks.
Assignment
Question 1: Marks 10
Consider the following scenarios and identify which Security Requirements could be applied to each of scenario.
1- A Dr finds that the patient history is wrong. Hospital information software DETECTS from its log that a nurse has altered that history of patient.
2- ATM service is down since morning.
3- Ali did not use his credit card on Sunday but still he received an email which tell him that his credit card has been used.
4- A student has got his university card, but with a picture of some other student on it.
5- The personal information provided by the customer on web page do not match with his actual NIC that he is carrying.
Question # 2 on next page.Question 2: Marks 10
Keeping in mind the different administrative approaches for information security and expected attack for information retrieval, you are required to select the correct option in column B for each case of column A. Write your option in column C.

Best of Luck!
@zareen said in CS315 Assignment 1 Solution and Discussion:
A student has got his university card, but with a picture of some other student on it.
The CPU of another computer was done-in by an overdose of acid and a set of wire snips. … University students in Massachusetts captured a computer center and used it … in assessing his physical security risks and then planning and implementing … The picture badge had its day but it allowed an assortment of “apes and …
@zareen said in CS315 Assignment 1 Solution and Discussion:
The personal information provided by the customer on web page do not match with his actual NIC that he is carrying.
This policy sets out how we will treat your personal information and explains how we … A cookie is a text file that is placed on your hard disk by a web page server. … It does not correspond to any user ID in your web application, and does not store any …
-
Assignment No. 01
Semester: Fall 2019
Network Security-CS315 Total Marks: 20Due Date: 15/11/2019
Instructions:
Please read the following instructions carefully before submitting assignment:
You need to use MS word document to prepare and submit the assignment on VU-LMS.
It should be clear that your assignment will not get any credit if: The assignment is submitted after due date.
The assignment is not in the required format (doc or docx)
The submitted assignment does not open or file is corrupt.
Assignment is copied (partial or full) from any source (websites, forums, students, etc)Objective:
To learn about Network Security Requirements and administrative tasks.
Assignment
Question 1: Marks 10
Consider the following scenarios and identify which Security Requirements could be applied to each of scenario.
1- A Dr finds that the patient history is wrong. Hospital information software DETECTS from its log that a nurse has altered that history of patient.
2- ATM service is down since morning.
3- Ali did not use his credit card on Sunday but still he received an email which tell him that his credit card has been used.
4- A student has got his university card, but with a picture of some other student on it.
5- The personal information provided by the customer on web page do not match with his actual NIC that he is carrying.
Question # 2 on next page.Question 2: Marks 10
Keeping in mind the different administrative approaches for information security and expected attack for information retrieval, you are required to select the correct option in column B for each case of column A. Write your option in column C.

Best of Luck!
Q.1
Consider the following scenarios and identify which Security Requirements could be applied to each of scenario.Q.1 Solution:
1- A Dr finds that the patient history is wrong. Hospital information software DETECTS from its log that a nurse has altered that history of patient.- Accountability
2- ATM service is down since morning.
- Availability
3- Ali did not use his credit card on Sunday but still he received an email which tell him that his credit card has been used.
- Confidentiality
4- A student has got his university card, but with a picture of some other student on it.
- Integrity
5- The personal information provided by the customer on web page do not match with his actual NIC that he is carrying.
- Authenticity
Q.2
Keeping in mind the different administrative approaches for information security and expected attack for information retrieval, you are required to match the case of column A to the column B.
Q.2 Solution:
-



