CS204 Assignment 2 Solution and Discussion
-
Assignment No. 02
Semester: Fall 2019
Cyber Law – CS204Total Marks: 15
Due Date:02/12/2019
Objective:
The objective of this assignment is to understand the concept of cyber security, its need, major security problems and the usage of cryptography technique for security purposes.
Instructions:
Please read the following instructions carefully before submitting the assignment:
You will submit your assignment before or on due date on VU-LMS.
Assignment sent via Email will not be accepted/graded in any case.
If the submitted assignment does not open or file is corrupt, it will not be graded.
Assignment should be completed by your own efforts it should not be copied from internet, handouts or books.
You will submit solution only in the Microsoft Word File.
Assignment is covered from lectures 04 to 06.
For any query about the assignment, contact at cs204@vu.edu.pkAssignment Questions
Questions: Marks 15
Question. 1 (05 Marks)
Read the following scenario carefully and answer the questions.
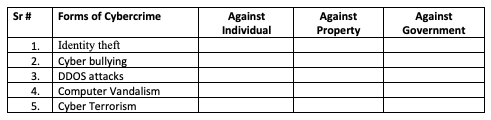
An employee of XYZ company get subscription to some number of free online IT magazines. During the process of registration for subscription, some information was being asked by the IT magzines in the form of questions, The IT magzines demand for bank details, first magazine asked for his complete date of birth, the second magazine asked for his bank name, and a third asked for his mother’s name.You are required to identify the possible cyber crime going on there also mention at least one prevention measure?
Question.2 (10 Marks)Use the caesar cipher method to encrypt the word “ACTIVATION” and show the complete process step by step.
Best of Luck
-
Assignment No. 02
Semester: Fall 2019
Cyber Law – CS204Total Marks: 15
Due Date:02/12/2019
Objective:
The objective of this assignment is to understand the concept of cyber security, its need, major security problems and the usage of cryptography technique for security purposes.
Instructions:
Please read the following instructions carefully before submitting the assignment:
You will submit your assignment before or on due date on VU-LMS.
Assignment sent via Email will not be accepted/graded in any case.
If the submitted assignment does not open or file is corrupt, it will not be graded.
Assignment should be completed by your own efforts it should not be copied from internet, handouts or books.
You will submit solution only in the Microsoft Word File.
Assignment is covered from lectures 04 to 06.
For any query about the assignment, contact at cs204@vu.edu.pkAssignment Questions
Questions: Marks 15
Question. 1 (05 Marks)
Read the following scenario carefully and answer the questions.
An employee of XYZ company get subscription to some number of free online IT magazines. During the process of registration for subscription, some information was being asked by the IT magzines in the form of questions, The IT magzines demand for bank details, first magazine asked for his complete date of birth, the second magazine asked for his bank name, and a third asked for his mother’s name.You are required to identify the possible cyber crime going on there also mention at least one prevention measure?
Question.2 (10 Marks)Use the caesar cipher method to encrypt the word “ACTIVATION” and show the complete process step by step.
Best of Luck
@zareen said in CS204 Assignment 1 Solution and Discussion:
Use the caesar cipher method to encrypt the word “ACTIVATION” and show the complete process step by step.
Encryption Key Management is crucial for securing your cryptographic keys. … Key Use and Rollover (Activation through Post-Activation) encrytion key … by authorized systems and users for encryption or decryption processes. … Here are the steps an encryption key manager vendor must to take to show full compliance:.link text
-
Assignment No. 02
Semester: Fall 2019
Cyber Law – CS204Total Marks: 15
Due Date:02/12/2019
Objective:
The objective of this assignment is to understand the concept of cyber security, its need, major security problems and the usage of cryptography technique for security purposes.
Instructions:
Please read the following instructions carefully before submitting the assignment:
You will submit your assignment before or on due date on VU-LMS.
Assignment sent via Email will not be accepted/graded in any case.
If the submitted assignment does not open or file is corrupt, it will not be graded.
Assignment should be completed by your own efforts it should not be copied from internet, handouts or books.
You will submit solution only in the Microsoft Word File.
Assignment is covered from lectures 04 to 06.
For any query about the assignment, contact at cs204@vu.edu.pkAssignment Questions
Questions: Marks 15
Question. 1 (05 Marks)
Read the following scenario carefully and answer the questions.
An employee of XYZ company get subscription to some number of free online IT magazines. During the process of registration for subscription, some information was being asked by the IT magzines in the form of questions, The IT magzines demand for bank details, first magazine asked for his complete date of birth, the second magazine asked for his bank name, and a third asked for his mother’s name.You are required to identify the possible cyber crime going on there also mention at least one prevention measure?
Question.2 (10 Marks)Use the caesar cipher method to encrypt the word “ACTIVATION” and show the complete process step by step.
Best of Luck
@zareen said in CS204 Assignment 1 Solution and Discussion:
An employee of XYZ company get subscription to some number of free online IT magazines. During the process of registration for subscription, some information was being asked by the IT magzines in the form of questions, The IT magzines demand for bank details, first magazine asked for his complete date of birth, the second magazine asked for his bank name, and a third asked for his mother’s name.You are required to identify the possible cyber crime going on there also mention at least one prevention measure?
Each car has associated with it zero to any number of recorded accidents. Answer : … are data-driven and sometimes used in executive information systems. … A study of online trading of few selected broking companies in. Pune. … paid an annual subscription fee of $89 to receive free shipping on all purchases through …link text
-
Use the caesar cipher method to encrypt the word “ACTIVATION” and show the complete process step by step.
A B C D E F G H I K L M N O P Q R S T U V W X Y Z
Chose a number form 1 to 26 .the number will represent the key or the “shift” value that will be used to shift the standard Alphabet.
KEY= 4
A B C D E F G H I K L M N O P Q R S T U V W X Y Z
W X Y Z A B C D E F G H I K L M N O P Q R S T U V
Now bottom row of ALPHABE will now by known as Cipher ALPHABET.
KEY=4
Message =”ACTIVATION”
Plain : A B C D E F G H I K L M N O P Q R S T U V W X Y Z
Cipher: W X Y Z A B C D E F G H I K L M N O P Q R S T U V
Ciper text : WYPERWPEKI